Exploring the Internet Access Policy
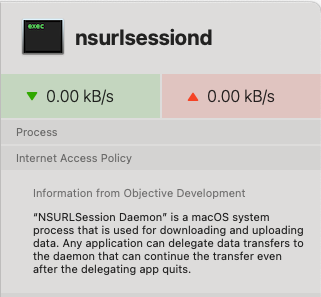
Reviewing Little Snitch and the enrichment it provides with Research Assistant1 about network connections. Research Assistant pulls from the Objective Dev database, but also allows developers the ability to write these definitions themselves called an Internet Access Policy.
Internet Access Policy’s2 (IAP) are declarations of intent and purpose for network connections from the developers. The declarations themselves are formalised around standards set by Objective Dev (love ya work!).
This dataset could be super helpful when reviewing a process tree during malware triage. Let’s explore.
Sample Internet Access Policy
...
<key>Connections</key>
<array>
<dict>
<key>IsIncoming</key>
<false/>
<key>Host</key>
<string>
dictionary1.mycompany.com, dictionary2.mycompany.com
</string>
<key>NetworkProtocol</key>
<string>TCP</string>
<key>Port</key>
<string>80, 443</string>
<key>Relevance</key>
<string>Essential</string>
<key>Purpose</key>
<string>
EditHelper updates its dictionary from this server.
</string>
<key>DenyConsequences</key>
<string>
If you deny these connections, dictionary and spell checker services may not be available or data may be outdated.
</string>
</dict>
...
Sample: https://help.obdev.at/littlesnitch5/files/InternetAccessPolicy.plist
Is there any known malware with an IAP?3
content:"InternetAccessPolicy.plist" AND p:1+
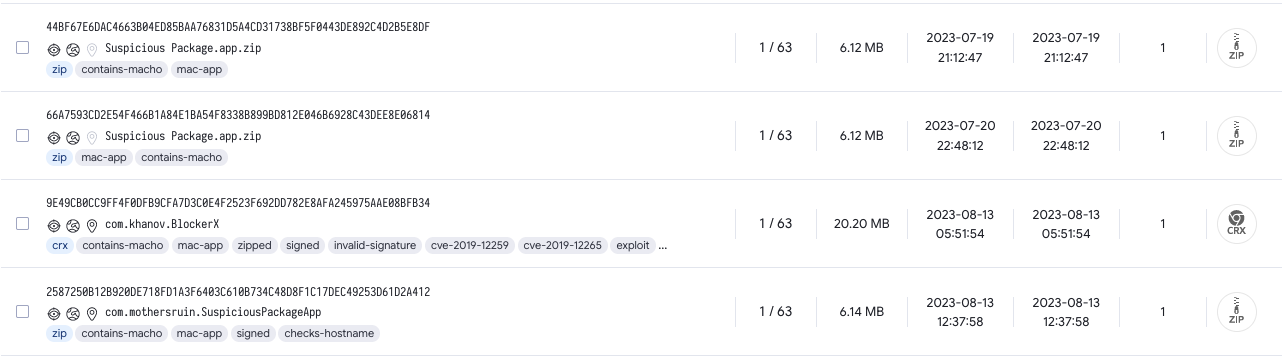
Triaging three of the four samples, it’s observed that these are most likely PUPs. The final detector seems to be a false positive, so the presence of an IAP is more likely an indicator of good-ness.
Is there anything not signed that has an IAP?4
content:"InternetAccessPolicy.plist" AND NOT tag:signed AND type:macho
Signed executables are usually an indicator of goodness; does an IAP extend that goodness? Unfortunately not, our experiment shows that there is likely no additional benefit vs reviewing signatures.